Hyperfox is a security auditing tool that proxies and records HTTP traffic between two hosts.
malfunkt/hyperfox
HTTP/HTTPs MITM tool with on-the-fly TLS cert generation. - malfunkt/hyperfox
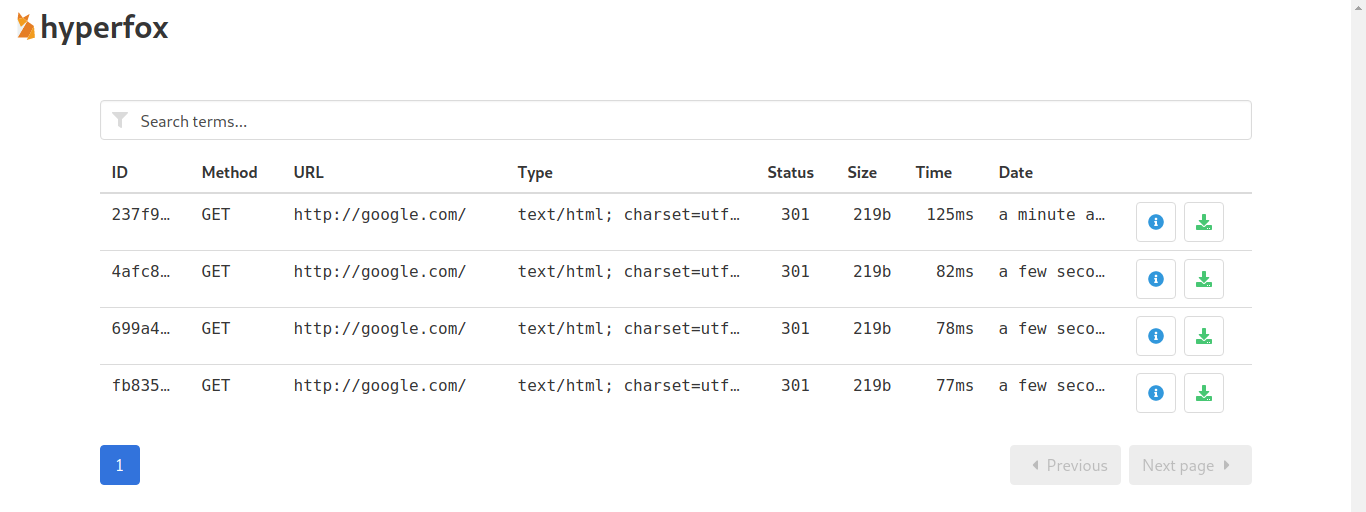
Hyperfox is a security auditing tool that proxies and records HTTP traffic between two hosts.
